My home office is actually just a desk in the den. The den also has a soft comfy couch, fireplace, and a large TV. This makes it a popular room for my teenager and her friends. It is also a place where the family relaxes and watches TV at night. Because of this traffic, people often want to use my computer. So I started looking for a way to allow guest access to my system. Preferably, an account that does not save anything, cannot install anything and leaves no trace of the person when they log out. This is when I happened upon the xguest package.
xguest - Least Privileged X User
The xguest package creates a Guest account with a special SELinux (Security Enhanced Linux) policy. It uses this policy to control the user's access. The user is very restricted and can basically log in and use a browser to access the internet. The SELinux policy also restricts a lot of network ports (like SSH connections) but allows most local applications to run. Also, nothing is saved past the current session. Xguest generates a temporary file system when the Guest account logs in, and it's destroyed when they log out. This means that when the xguest user logs off, or the system rebooted, anything created by the user is gone (cookies, files, cache, etc.).
The xguest user account was designed as a least privilege account for use on kiosks and other open systems that require a graphical interface. The SELinux policy can be changed (and booleans set) to further restrict or expand the users permissions.
This was tested on Red Hat 8, CentOS 7 and Fedora 31. The package is available to all three of these systems. As far as I can tell, the xguest package is not available on Ubuntu.
Pros
- Great for Security
- No access to sudo or su
- Cannot access regular users data or configuration files
- Very restrictive out of the box (SSH, and other common ports are blocked)
- Allows user to run most local applications (Browsers, Libre Office, etc..)
- Very flexible (w/ SELinux knowledge)
- Simple to install and use
Cons
- SELinux has a steep learning curve, not very friendly
- Seems to only be available or Red Hat variants
- Gnome specific utility - Gnome is the default display manager for Red Hat, CentOS, Fedora and other Red Hat variants
Prerequisites for xguest
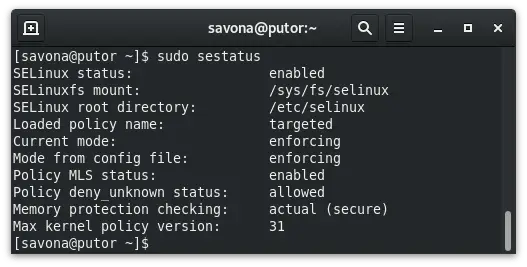
As discussed above, the xguest packages uses SELinux to secure the Guest account. In order for this to happen, you MUST have SELinux enabled and in enforcing mode. You can check the SELinux status using the sestatus command.
In addition, you must be using the Gnome Display Manager. Gnome is the default display manager for Red Hat, CentOS, Fedora and most other Red Hat variants.
Installing the xguest Package
You can easily install the xguest package using yum or dnf package managers.
Installing xguest with yum (CentOS 7 / Red Hat 7)
sudo yum install xguestInstalling xguest with dnf (Red Hat 8, CentOS 8, Fedora)
sudo dnf install xguest Available Booleans for xguest Account
There are several pre-defined booleans to allow flexibility for the xguest account. Here are some of the more popular booleans. For a complete list of booleans and allowed tcp ports see the man page in the resources and links section below.
- xguest_mount_media - Allows guest to mount removable media
- xguest_connect_network - Allow xguest to confgure Network Manager, connect to wifi, etc
- xguest_exec_content - Allow xguest to execute files in their home directory and tmp
- xguest_use_bluetooth - Allow xguest to use bluetooth devices
Logging In as Guest
There is no configuration necessary once the package is installed. You will see a user named "Guest" on your GDM login screen. Simply click the user to log in.
The Guest user can now surf the internet, log into their email, and basically do anything within Firefox. They can save files, create documents and send them via email, etc. Once they log out, all of it is gone.
Caveats and Workarounds
One thing that I came across working with the xguest is the Gnome initial setup runs every time the Guest account logs in. This is annoying, especially when I was using the system for a Kiosk. If you have the same problem read "Disable Gnome Initial Setup Screen".
Conclusion
The xguest package worked great for creating a non-privileged account for house guests to use. I have also used it on other projects, including to create check-in kiosks at a local business. If you have experience with SELinux you can really lock it down to only what is required to accomplish a specific task.
Resources and Links
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed.
3 Comments
Join Our Newsletter
Categories
- Bash Scripting (17)
- Basic Commands (51)
- Featured (7)
- Just for Fun (5)
- Linux Quick Tips (98)
- Linux Tutorials (65)
- Miscellaneous (15)
- Network Tools (6)
- Reviews (2)
- Security (32)
- Smart Home (1)


Thanks for posting this. I'm unable to get a desktop after choosing guest.
I've seen many old threads dating back to Fedora 19 about the issue.
I fixed one error related to keyring.d, but I'm still unable to get past access denied:
avc: denied { open } for pid=5173 comm="gnome-shell" path="/etc/udev/hwdb.bin
What version of Fedora did you get this working on?
Do you have any suggestions?
Thanks again!
Eric
We tested this on Fedora 32. What are the errors you are getting?
I don't get any GUI errors, just a gray screen for a short period, then back to the login screen.
Here is the output of audit.log
type=SERVICE_START msg=audit(1596912333.194:972): pid=1 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='unit=fprintd comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'UID="root" AUID="unset"
type=USER_AUTH msg=audit(1596912333.199:973): pid=16647 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 msg='op=PAM:authentication grantors=pam_selinux_permit acct="xguest" exe="/usr/libexec/gdm-session-worker" hostname=localhost.localdomain addr=? terminal=/dev/tty1 res=success'UID="root" AUID="unset"
type=USER_ACCT msg=audit(1596912333.207:974): pid=16647 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 msg='op=PAM:accounting grantors=pam_unix,pam_localuser acct="xguest" exe="/usr/libexec/gdm-session-worker" hostname=localhost.localdomain addr=? terminal=/dev/tty1 res=success'UID="root" AUID="unset"
type=CRED_ACQ msg=audit(1596912333.218:975): pid=16647 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 msg='op=PAM:setcred grantors=pam_env,pam_localuser,pam_unix,pam_gnome_keyring acct="xguest" exe="/usr/libexec/gdm-session-worker" hostname=localhost.localdomain addr=? terminal=/dev/tty1 res=success'UID="root" AUID="unset"
type=LOGIN msg=audit(1596912333.234:976): pid=16647 uid=0 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 old-auid=4294967295 auid=1001 tty=(none) old-ses=4294967295 ses=27 res=1UID="root" OLD-AUID="unset" AUID="xguest"
type=USER_ROLE_CHANGE msg=audit(1596912333.236:977): pid=16647 uid=0 auid=1001 ses=27 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 msg='pam: default-context=xguest_u:xguest_r:xguest_t:s0 selected-context=xguest_u:xguest_r:xguest_t:s0 exe="/usr/libexec/gdm-session-worker" hostname=localhost.localdomain addr=? terminal=/dev/tty2 res=success'UID="root" AUID="xguest"
type=AVC msg=audit(1596912333.333:978): avc: denied { getattr } for pid=16677 comm="chown" name="/" dev="tmpfs" ino=12725730 scontext=system_u:system_r:namespace_init_t:s0-s0:c0.c1023 tcontext=system_u:object_r:tmpfs_t:s0 tclass=filesystem permissive=0
type=AVC msg=audit(1596912333.333:979): avc: denied { getattr } for pid=16677 comm="chown" name="/" dev="tmpfs" ino=12725730 scontext=system_u:system_r:namespace_init_t:s0-s0:c0.c1023 tcontext=system_u:object_r:tmpfs_t:s0 tclass=filesystem permissive=0
type=SERVICE_START msg=audit(1596912333.471:980): pid=1 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='unit=user-runtime-dir@1001 comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'UID="root" AUID="unset"
type=USER_ACCT msg=audit(1596912333.505:981): pid=16688 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='op=PAM:accounting grantors=pam_unix,pam_localuser acct="xguest" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'UID="root" AUID="unset"
type=CRED_ACQ msg=audit(1596912333.506:982): pid=16688 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='op=PAM:setcred grantors=? acct="xguest" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=failed'UID="root" AUID="unset"
type=USER_ROLE_CHANGE msg=audit(1596912333.507:983): pid=16688 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='pam: default-context=xguest_u:xguest_r:xguest_t:s0 selected-context=xguest_u:xguest_r:xguest_t:s0 exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'UID="root" AUID="unset"
type=LOGIN msg=audit(1596912333.508:984): pid=16688 uid=0 subj=system_u:system_r:init_t:s0 old-auid=4294967295 auid=1001 tty=(none) old-ses=4294967295 ses=28 res=1UID="root" OLD-AUID="unset" AUID="xguest"
type=USER_START msg=audit(1596912333.518:985): pid=16688 uid=0 auid=1001 ses=28 subj=system_u:system_r:init_t:s0 msg='op=PAM:session_open grantors=pam_selinux,pam_selinux,pam_loginuid,pam_keyinit,pam_limits,pam_systemd,pam_unix acct="xguest" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=success'UID="root" AUID="xguest"
type=ANOM_ABEND msg=audit(1596912333.522:986): auid=1001 uid=1001 gid=1001 ses=28 subj=xguest_u:xguest_r:xguest_t:s0 pid=16688 comm="systemd" exe="/usr/lib/systemd/systemd" sig=11 res=1AUID="xguest" UID="xguest" GID="xguest"
type=SERVICE_START msg=audit(1596912333.525:987): pid=1 uid=0 auid=4294967295 ses=4294967295 subj=system_u:system_r:init_t:s0 msg='unit=user@1001 comm="systemd" exe="/usr/lib/systemd/systemd" hostname=? addr=? terminal=? res=failed'UID="root" AUID="unset"
type=USER_START msg=audit(1596912333.574:988): pid=16647 uid=0 auid=1001 ses=27 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 msg='op=PAM:session_open grantors=pam_selinux,pam_loginuid,pam_selinux,pam_keyinit,pam_namespace,pam_keyinit,pam_limits,pam_systemd,pam_unix,pam_gnome_keyring,pam_umask acct="xguest" exe="/usr/libexec/gdm-session-worker" hostname=localhost.localdomain addr=? terminal=/dev/tty2 res=success'UID="root" AUID="xguest"
type=USER_LOGIN msg=audit(1596912333.575:989): pid=16647 uid=0 auid=1001 ses=27 subj=system_u:system_r:xdm_t:s0-s0:c0.c1023 msg='uid=1001 exe="/usr/libexec/gdm-session-worker" hostname=? addr=? terminal=? res=success'UID="root" AUID="xguest" UID="xguest"
type=AVC msg=audit(1596912335.264:990): avc: denied { open } for pid=16819 comm="gnome-shell" path="/etc/udev/hwdb.bin" dev="sda3" ino=656744 scontext=xguest_u:xguest_r:xguest_t:s0 tcontext=system_u:object_r:systemd_hwdb_etc_t:s0 tclass=file permissive=0